The CIA Triad Security Model
With the increasing sophistication of cyber threats facing organizations and businesses critical infrastructure and sensitive data, it’s now more important than ever to adopt a comprehensive cloud security governance model. To put this in a monetary context, it’s estimated that the average cost of a data breach for a company in the United States is $7.91 million1; money spent to cover the costs of forensic analysis, remediation and litigation. Proactively addressing gaps in your overall security posture can save an organization a lot of unnecessary pain and expense.
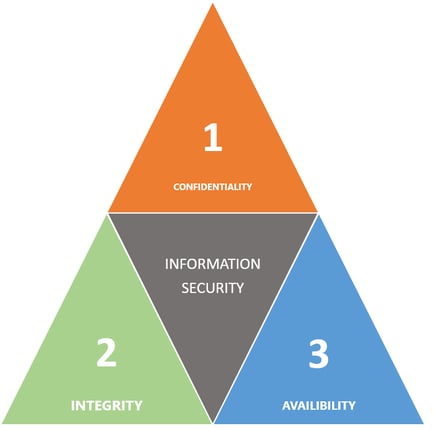
The good news is you don’t have to reinvent the wheel to build out a comprehensive governance model for your organization. The CIA Triad is a well-known and venerable model that can help you think through all of the facets of building a strong security posture. The model consists of these three core concepts
Confidentiality
Confidentiality is concerned with preventing unauthorized access to sensitive information. The access could be intentional, such as a bad actor breaking into the network and stealing the information, or it could be unintentional, as the result of carelessness or lack of knowledge on the part of individuals handling the information. When planning a strategy to mitigate these risks, be sure to include cryptography and access control. Some Azure services and feature that will help you maintain the confidentiality of your critical information include:
- Certificates for all websites and api endpoints
- TDE performs real-time I/O encryption and decryption of the data at the page level.
- Transport Layer Security (TLS) is also used for all communication in addition to the base transport level checksums provided by TCP/IP.
Integrity
The integrity component of the CIA Triad is concerned with protecting data from modification or deletion by unauthorized users. When performing analysis to identify who should have access to what, be sure to also note whether your data should be immutable or not. There are some types of data that should never change (such as audit logs and event logs).
- Data Integrity Alert Monitoring
- Azure Information Protection for Azure SQL Database, Azure SQL Managed Instance, and Azure Synapse Analytics
- Log immutability and traceability
- RBAC
Availability
The last component in the CIA Triad refers to Availability. Reliable access to access and authentication mechanisms (think AAD) must all be working properly for the information they provide and protect to be available when needed. There are architectural patterns and practices that can be employed to guarantee availability which are all supported by Azure including:
- Setting up high availability clusters
- Azure Front Door and Traffic Manager for intelligent routing and rerouting during network outages
- To protect against Distributed Denial of Service attacks and other common exploits, leverage Azure Application Gateway, Azure Firewall and Web Application Firewall.
- Also take time to configure Service Level Agreements that make sense for your business or organization’s use cases. Rapid disaster recovery is something every organization should carefully plan out.
While this model helps teams think about security, its not intended to be an all-encompassing framework. InCycle Software has worked with many clients to help them plan out their security governance policies. and accelerate their security governance adoption.
To learn more about enterprise and cloud governance, download the Governance Playbook today!