Collaborative Cloud Governance - Auditability and Visibility
Over the last decade we’ve seen automobile manufacturers bring to market a number of advanced safety systems that help save lives and make driving a car a better experience. One safety feature I find especially useful is the blind spot warning system. If you’re not familiar with this system it uses cameras, radar, and/or ultrasonic sensors alongside your vehicle to detect vehicles you can’t see that are next to or behind your car. When a car enters your blind spot, a visual alert is displayed on your vehicle dashboard, helping you avoid the risk of pulling into the lane occupied by another car. In much the same way, Azure policies, auditing, and alerts provide a way to identify blind spots in your organization’s security posture and policy adherence.
Common use cases for Azure Policy include implementing governance for resource consistency, regulatory compliance, security, cost, and management. Policy definitions for these common use cases are already available in your Azure environment as built-ins to help you get started. Policy definitions can also be grouped together into initiatives, that align with your organizational governance strategy for the cloud.
Monitoring for Compliance
One of the biggest benefits of Azure Policy is the insight and controls it provides over resources in a subscription or management group of subscriptions. Once resources have been assigned to Azure policies, initiatives, or blueprints, they are available for compliance evaluation. By default, compliance scans will occur once every 24 hours. When the compliance scan takes place the effect event (append, audit, deny, deploy) and compliant status information for the individual resource are made available in the portal.
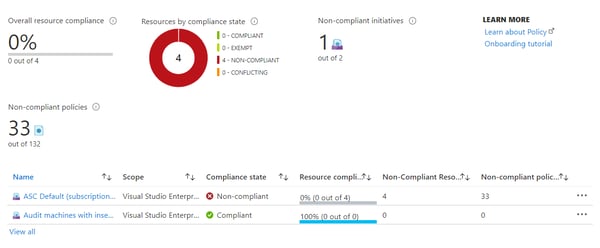 When setting up your policies you have the option to run a compliance check to report on or to remediate resources that are out of compliance. The policy compliance dashboard offers a robust view of your resources and their compliance state for the selected scopes.
When setting up your policies you have the option to run a compliance check to report on or to remediate resources that are out of compliance. The policy compliance dashboard offers a robust view of your resources and their compliance state for the selected scopes.
When you first setup your policies I highly recommend setting up an audit effect rather than deny tracking the impact of your policy definitions on your Azure resources.
Take the Wheel
Adding remediation step to your policy definitions is akin to giving your blind spot warning system the ability to steer you out of trouble. Resources that are non-compliant can be reviewed according to the resource scope (subscription, management group, resource group, or individually) and optionally a location. A list of policy definitions that have non-compliant resources are displayed. If you choose you can run the deployIfNotExists effect or the modify operations of the assigned policy on your existing resources.
For organizations interested in empowering innovation and agile adoption of Azure cloud services, InCycle can accelerate your efforts towards auditability and visibility of all your cloud resources/ How are you managing your resources in Azure? Ask yourself some simple questions:
- Do you know where your Azure resources are being created?
- Are your resource provisioning standards consistent?
- Are you able to audit and enforce consistent provisioning policies?
- Can you decommission projects with confidence?
- Can you recreate resources in Azure with confidence?
If you don’t know the answers to these questions you may have cloud governance blind spots. Download our Azure Governance Playbook today to more tips on modern governance.










