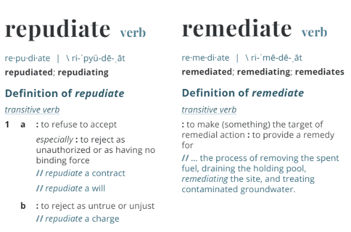
Repudiate or Remediate?
 Deployments in Azure have a few methodologies by which they can be governed based on sets of rules which taken together are called policies. When policy rules are violated effects can be used to deny deployment. When a deployment is denied it is repudiated by Azure at the earliest possible moment without any change to your azure infrastructure. Other policy effects are available which will allow the deployment to succeed but with warnings.
Deployments in Azure have a few methodologies by which they can be governed based on sets of rules which taken together are called policies. When policy rules are violated effects can be used to deny deployment. When a deployment is denied it is repudiated by Azure at the earliest possible moment without any change to your azure infrastructure. Other policy effects are available which will allow the deployment to succeed but with warnings.
What About Everything Else?
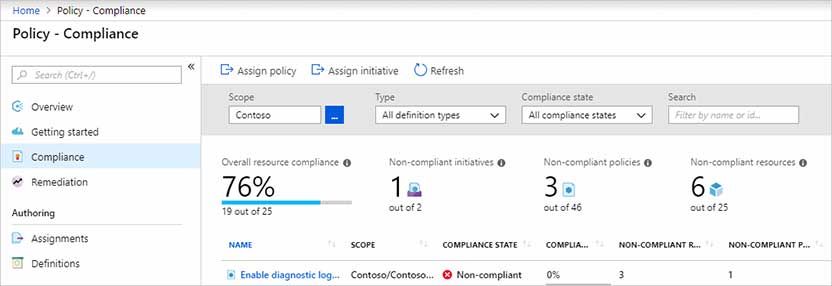
If you’re an Azure early adopter, you may not have self-governed as well as you would have hoped. From a maturity perspective, not all options available to you today would have been available in 2008 for automated governance. So, what about all those resources running around in Azure today? Azure is inherently fungible, more than likely your earliest resources are no longer around, either from deprecation of resources, or end of life projects. Those stragglers? They are beyond repudiation at this point, they already exist! They are not beyond remediation. We can still audit and remediate those resources to bring them into compliance.
Turn on TLS 1.2
All Azure services currently support TLS 1.2, but this was not always the case. We could build a remediation policy that would update all non-compliant resources to use the newer version of TLS. In cases where this is not desirable, we can limit the scope to a management group, subscription, or resource group. Creating a policy remediation in Azure can feel complicated, but with some well-defined scripts and processes we can easily execute those boilerplate scripts for setup. The template for our remediation task would be similar to:
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Web/sites/config"
},
{
"field": "Microsoft.Web/sites/config/minTlsVersion",
"notEquals": "1.2"
}
]
},
"then": {
"effect": "modify",
"details": {
"roleDefinitionIds": [
"/providers/microsoft.authorization/roleDefinitions/b24988ac-6180-42a0-ab88-20f7382dd24c"
],
"operations": [{
"operation": "addOrReplace",
"field": "Microsoft.Web/sites/config/minTlsVersion",
"value": "1.2"
}]
}
}
}
Setting up a Remediation
There are some tasks that need to be accomplished to remediate a policy within Azure. They can be accomplished through the Azure Portal, the Azure Command Line Interface. The remediation will use a Managed Identity to handle any deployments that may be required for remediation. When using the portal in most circumstances the managed identity will be created for you but using other artifices such as Azure CLI or PowerShell require you to manually create the managed identity. Additionally, a remediation task will need to be created.
Governance as Code
While it may seem, there is a lot of work in setting up a remediation, there is a degree of boilerplate code that can be stored, parameterized, and reused.
- Define Remediation Policy
- Create and Configure a Managed Identity
# Login first with Connect-AzAccount if not using Cloud Shell
# Get the built-in "Deploy SQL DB transparent data encryption" policy definition
$policyDef = Get-AzPolicyDefinition -Id '/providers/Microsoft.Authorization/policyDefinitions/86a912f6-9a06-4e26-b447-11b16ba8659f'
# Get the reference to the resource group
$resourceGroup = Get-AzResourceGroup -Name $resourceGroupName
# Create the assignment using the -Location and -AssignIdentity properties
$assignment = New-AzPolicyAssignment -Name $policyAssignmentName -DisplayName $policyDisplayName -Scope $resourceGroup.ResourceId -PolicyDefinition $policyDef -Location $region -AssignIdentity
# Use the $policyDef to get to the roleDefinitionIds array
$roleDefinitionIds = $policyDef.Properties.policyRule.then.details.roleDefinitionIds
if ($roleDefinitionIds.Count -gt 0)
{
$roleDefinitionIds | ForEach-Object {
$roleDefId = $_.Split("/") | Select-Object -Last 1 New-AzRoleAssignment -Scope $resourceGroup.ResourceId -ObjectId $assignment.Identity.PrincipalId -RoleDefinitionId $roleDefId
}
}
- Create a Remediation Task
# Login first with Connect-AzAccount if not using Cloud Shell
# Create a remediation for a specific assignment
Start-AzPolicyRemediation -Name 'myRemedation' -PolicyAssignmentId '/subscriptions/{subscriptionId}/providers/Microsoft.Authorization/policyAssignments/{myAssignmentId}'
- Are you certain that all resources are compliant with your policies?
- Have you audited your resources with your policies?
- Are you ready to take the next steps and download the Azure Governance Playbook?
For organizations interested in managing compliance of their governance strategy, InCycle can accelerate your efforts. How are you managing your resources in Azure? Ask yourself some simple questions:
- Do you know where your Azure resources are being created?
- Are your resource provisioning standards consistent?
- Are you able to audit and enforce consistent provisioning policies?
- Can you decommission projects with confidence?
- Can you recreate resources in Azure with confidence?